siemsoar
The average SOC gets 4,484 alerts per day and ignores most of them. That's autoimmune disease, not a detection gap. How Jerne's Immune Network Theory maps onto graph-based architectures that suppress noise instead of generating more of it.
February 21, 20268 min read
supply chain3R model
From the siege of Kirrha to SolarWinds, attackers bypass walls by compromising what's already trusted. Why authentication proves provenance but not intent, and how to allocate scarce verification budget across a dependency graph you'll never fully see.
February 13, 20268 min read
graph theorysecurity architecture
The Củ Chi tunnels were 250 kilometers of passages dug with shovels. The US had satellites. The tunnels worked because they exploited topology, not topography. Attackers still do.
February 4, 20268 min read
zero trustnetwork security
The firewall-first mindset creates fragile networks that collapse on breach. Designing firewall-last forces you to build self-defending nodes, prune unnecessary connections, and treat the perimeter as defense in depth—not a structural dependency.
February 2, 20268 min read
zero trustgraph theory
Every vendor is selling Zero Trust. None of them are selling graph databases. That's the problem. You can't determine 'necessary edges' without mapping your current graph—and no identity proxy solves that.
January 23, 20268 min read
threat modelingattack modeling
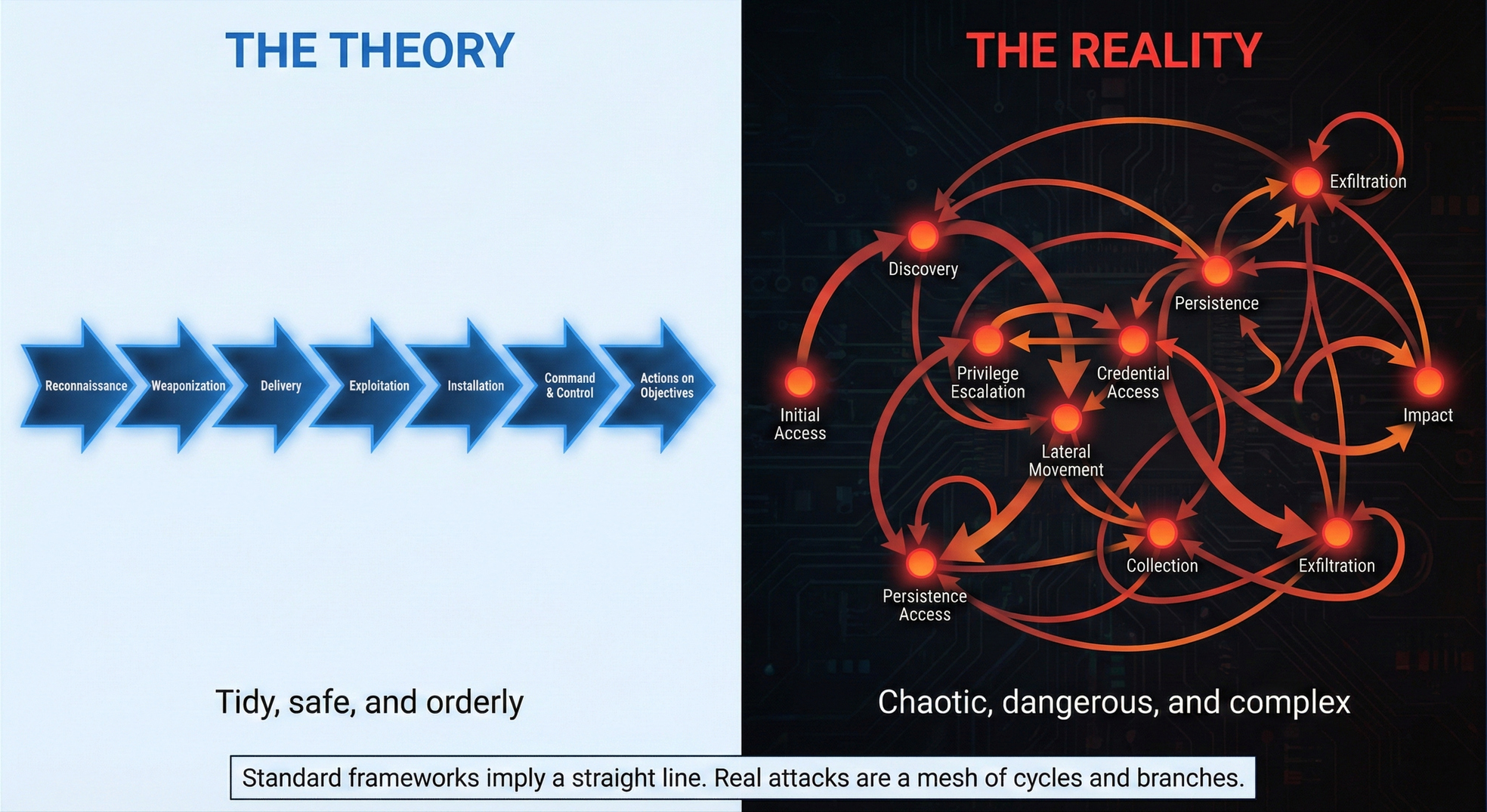
The Kill Chain shows attacks as linear progressions. Real attacks loop through lateral movement, branch based on what they find, and restart tactics on every new system. Graph theory models what linear frameworks can't.
January 12, 20268 min read
graph theoryperimeter security
The Spartans built the perfect defensive chokepoint—and were destroyed by a path they didn't know existed. Graph theory reveals why perimeter security fails and what modern defenders must do instead
January 8, 20268 min read
graph theorysecurity architecture
You cannot optimize what you cannot measure. Security teams ask graph theory questions—attack paths, blast radius, chokepoints—but use tools built for lists. Here's why that gap is costing you.
December 29, 20258 min read
risk managementorganizational design
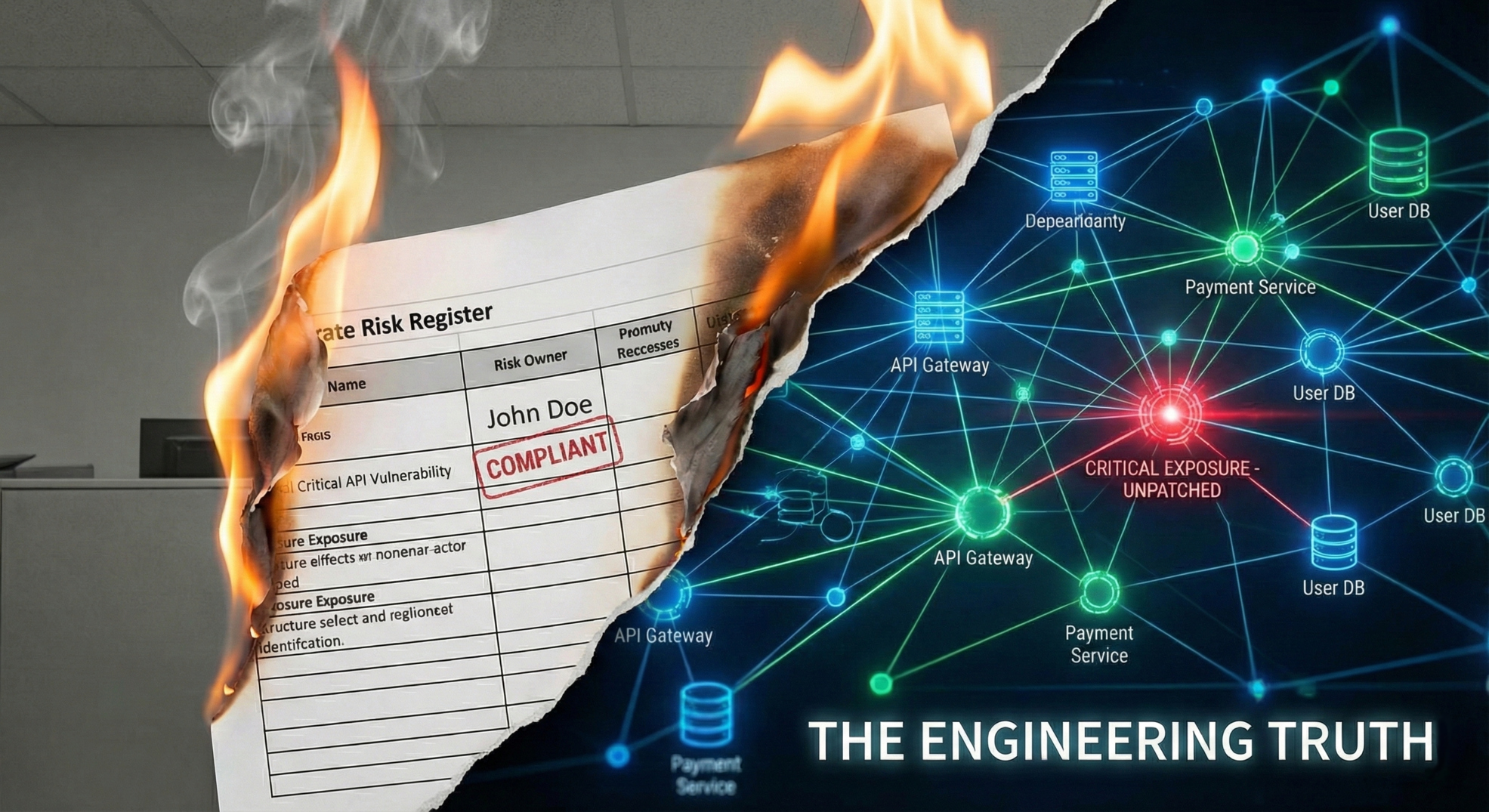
Risk owner' sounds like a real role, but it's often just a name in a cell. True responsibility requires personal stakes: authority to act, accountability for outcomes, and capability to execute. Here's how to move from documentation to action.
December 17, 20258 min read
project managementeconomics
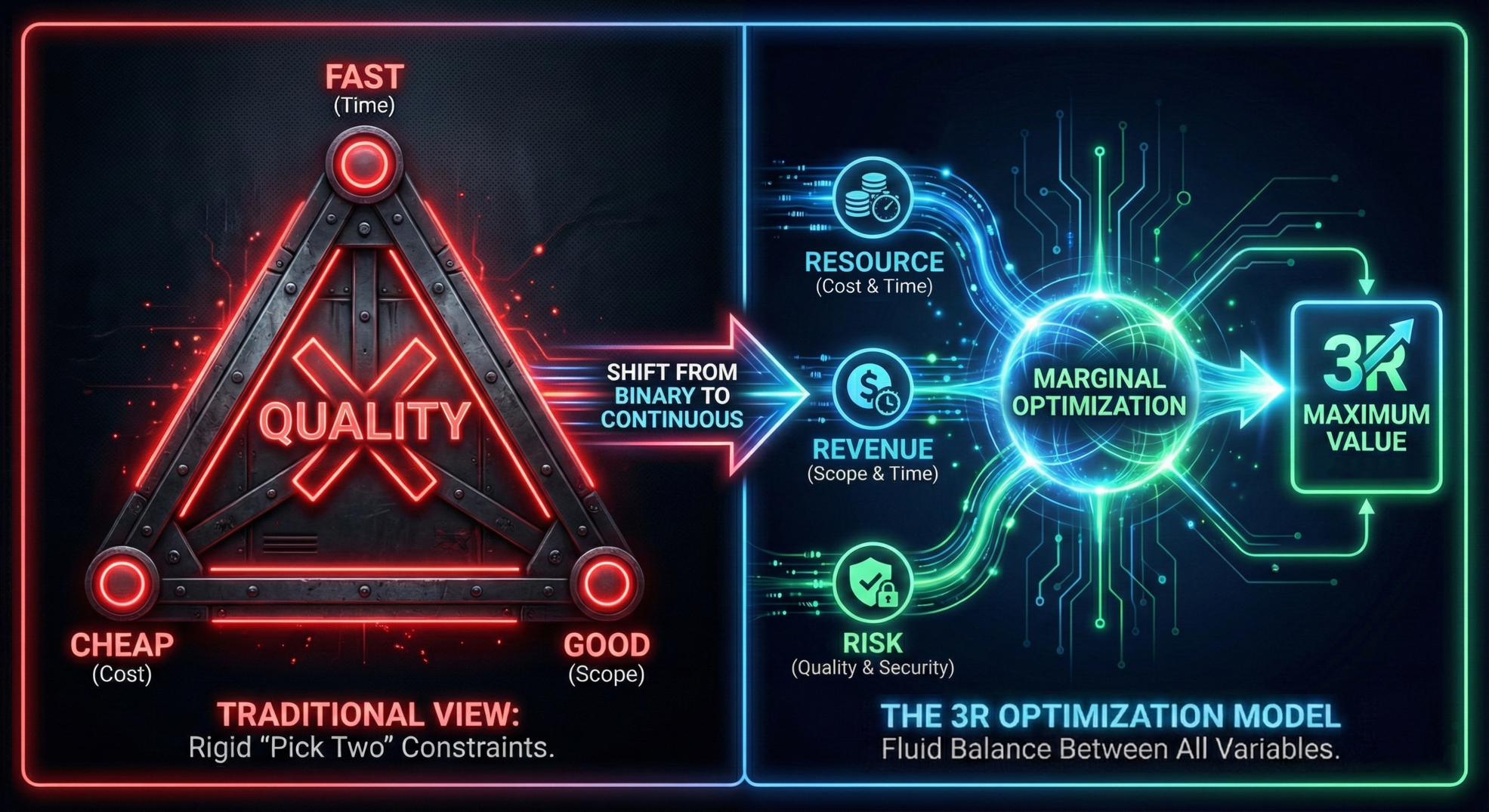
The Iron Triang le gives teams a convenient excuse for failure. The 3R Optimization Model—Revenue, Resources, Risk—forces them to do the math. Here's why marginal analysis beats binary trade-offs.
September 27, 20258 min read
risk managementeconomics
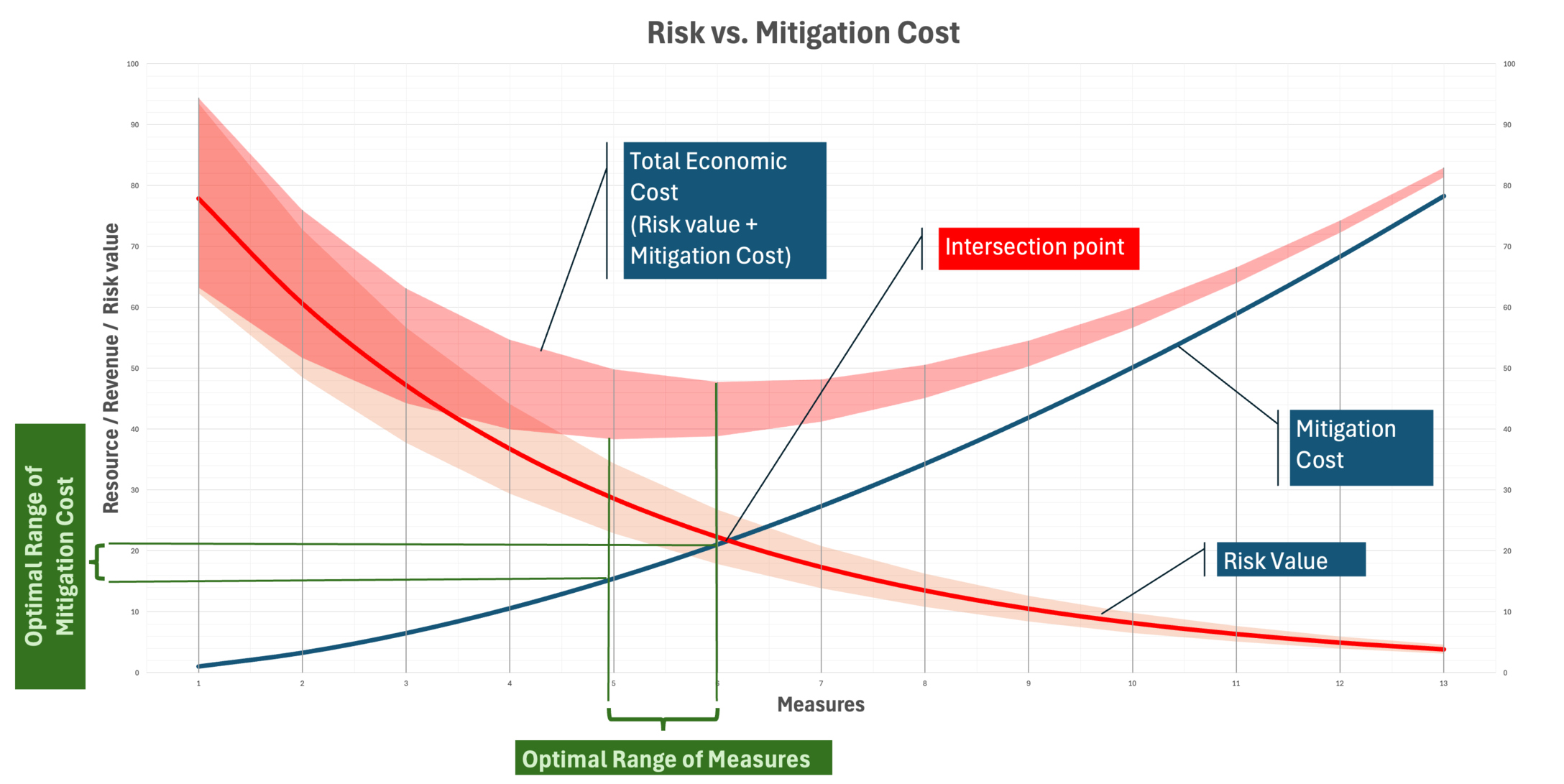
The optimal security investment isn't where cost equals risk—that's a common misconception. It's where the next dollar spent reduces risk by exactly one dollar. Here's how marginal analysis changes security decision-making.
September 27, 20258 min read